Critical vulnerabilities in BIG-IP appliances leave big networks open to intrusion
Getty Images
Researchers on Wednesday reported critical vulnerabilities in a widely used networking appliance that leaves some of the world’s biggest networks open to intrusion.
The vulnerabilities reside in BIG-IP Next Central Manager, a component in the latest generation of the BIG-IP line of appliances, which organizations use to manage traffic going into and out of their networks. Seattle-based F5, which sells the product, says its gear is used in 48 of the top 50 corporations as tracked by Fortune. F5 describes the Next Central Manager as a “single, centralized point of control” for managing entire fleets of BIG-IP appliances.
As devices performing load balancing, DDoS mitigation, and inspection and encryption of data entering and exiting large networks, BIG-IP gear sits at their perimeter and acts as a major pipeline to some of the most security-critical resources housed inside. Those characteristics have made BIG-IP appliances ideal for hacking. In 2021 and 2022, hackers actively compromised BIG-IP appliances by exploiting vulnerabilities carrying severity ratings of 9.8 out of 10.
On Wednesday, researchers from security firm Eclypsium reported finding what they said were five vulnerabilities in the latest version of BIG-IP. F5 has confirmed two of the vulnerabilities and released security updates that patch them. Eclypsium said three remaining vulnerabilities have gone unacknowledged and it’s unclear if their fixes are included in the latest release. Whereas the exploited vulnerabilities from 2021 and 2022 affected older BIG-IP versions, the new ones reside in the latest version, known as BIG-IP Next. The severity of both vulnerabilities is rated as 7.5.
“BIG-IP Next marks a completely new incarnation of the BIG-IP product line touting improved security, management, and performance,” Eclypsium researchers wrote. “And this is why these new vulnerabilities are particularly significant—they not only affect the newest flagship of F5 code, they also affect the Central Manager at the heart of the system.”
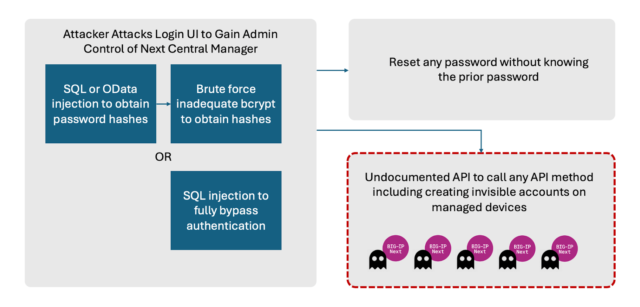
The vulnerabilities allow attackers to gain full administrative control of a device and then create accounts on systems managed by the Central Manager. “These attacker-controlled accounts would not be visible from the Next Central Manager itself, enabling ongoing malicious persistence within the environment,” Eclypsium said. The researchers said they have no indication any of the vulnerabilities are under active exploitation.
Both of the fixed vulnerabilities can be exploited to extract password hashes or other sensitive data that allow for the compromise of administrative accounts on BIG-IP systems. F5 described one of them—tracked as CVE-2024-21793—as an Odata injection flaw, a class of vulnerability that allows attackers to inject malicious data into Odata queries. The other vulnerability, CVE-2024-26026, is an SQL injection flaw that can execute malicious SQL statements.
Eclypsium said it reported three additional vulnerabilities. One is an undocumented programming interface that allows for server-side request forgeries, a class of attack that gains access to sensitive internal resources that are supposed to be off-limits to outsiders. Another is the ability for unauthenticated administrators to reset their password even without knowing what it is. Attackers who gained control of an administrative account could exploit this last flaw to lock out all legitimate access to a vulnerable device.
The third is a configuration in the bcrypt password hashing algorithm that makes it possible to perform brute-force attacks against millions of passwords per second. The Open Web Application Security Project says that the bcrypt “work factor”—meaning the amount of resources required to convert plaintext into cryptographic hashes—should be set to a level no lower than 10. When Eclypsium performed its analysis, the Central Manager set it at six.
Eclypsium researchers wrote:
The vulnerabilities we have found would allow an adversary to harness the power of Next Central Manager for malicious purposes. First, the management console of the Central Manager can be remotely exploited by any attacker able to access the administrative UI via CVE 2024-21793 or CVE 2024-26026. This would result in full administrative control of the manager itself. Attackers can then take advantage of the other vulnerabilities to create new accounts on any BIG-IP Next asset managed by the Central Manager. Notably, these new malicious accounts would not be visible from the Central Manager itself.
All 5 vulnerabilities were disclosed to F5 in one batch, but F5 only formally assigned CVEs to the 2 unauthenticated vulnerabilities. We have not confirmed if the other 3 were fixed at the time of publication.
F5 representatives didn’t immediately have a response to the report. Eclypsium went on to say:
These weaknesses can be used in a variety of potential attack paths. At a high level attackers can remotely exploit the UI to gain administrative control of the Central Manager. Change passwords for accounts on the Central Manager. But most importantly, attackers could create hidden accounts on any downstream device controlled by the Central Manager.
Eclypsium
The vulnerabilities are present in BIG-IP Next Central Manager versions 20.0.1 through 20.1.0. Version 20.2.0, released Wednesday, fixes the two acknowledged vulnerabilities. As noted earlier, it’s unknown if version 20.2.0 fixes the other behavior Eclypsium described.
“If they are fixed, it is +- okay-ish, considering the version with them will still be considered vulnerable to other things and need a fix,” Eclypsium researcher Vlad Babkin wrote in an email. “If not, the device has a long-term way for an authenticated attacker to keep their access forever, which will be problematic.”
A query using the Shodan search engine shows only three instances of vulnerable systems being exposed to the Internet.
Given the recent rash of active exploits targeting VPNs, firewalls, load balancers, and other devices positioned at the network edge, BIG-IP Central Manager users would do well to place a high priority on patching the vulnerabilities. The availability of proof-of-concept exploitation code in the Eclypsium disclosure further increases the likelihood of active attacks.
Source link
