After collecting $22 million, AlphV ransomware group stages FBI takedown
The ransomware group responsible for hamstringing the prescription drug market for two weeks has suddenly gone dark, just days after receiving a $22 million payment and standing accused of scamming an affiliate out of its share of the loot.
The events involve AlphV, a ransomware group also known as BlackCat. Two weeks ago, it took down Change Healthcare, the biggest US health care payment processor, leaving pharmacies, health care providers, and patients scrambling to fill prescriptions for medicines. On Friday, the bitcoin ledger shows, the group received nearly $22 million in cryptocurrency, stoking suspicions the deposit was payment by Change Healthcare in exchange for AlphV decrypting its data and promising to delete it.
Representatives of Optum, the parent company, declined to say if the company has paid AlphV.
Honor among thieves
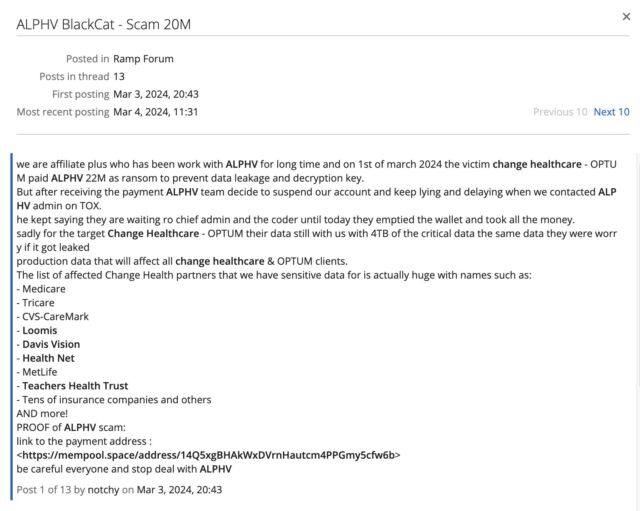
On Sunday, two days following the payment, a party claiming to be an AlphV affiliate said in an online crime forum that the nearly $22 million payment was tied to the Change Healthcare breach. The party went on to say that AlphV members had cheated the affiliate out of the agreed-upon cut of the payment. In response, the affiliate said it hadn’t deleted the Change Healthcare data it had obtained.
vxunderground
On Tuesday—four days after the bitcoin payment was made and two days after the affiliate claimed to have been cheated out of its cut—AlphV’s public dark web site started displaying a message saying it had been seized by the FBI as part of an international law enforcement action.

The UK’s National Crime Agency, one of the agencies the seizure message said was involved in the takedown, didn’t respond to an email seeking comment. Multiple other news organizations said NCA officials said the agency played no part in any such action. The denial, as well as evidence the seizure notice was copied from a different site and pasted into the AlphV one, has led multiple researchers to conclude the ransomware group staged the takedown and took the entire $22 million payment for itself.
“Since people continue to fall for the ALPHV/BlackCat cover up: ALPHV/BlackCat did not get seized,” Fabian Wosar, head of ransomware research at security firm Emsisoft, wrote on social media. “They are exit scamming their affiliates. It is blatantly obvious when you check the source code of the new takedown notice.”
Source link
